Get RCE With SSTI
Yo yo miss me right? Guess what Im back🥳🥳So lets talk about SSTI or Server-side template injection As usually we need to works with things before jumping into SSTI. So lets try a template engine and learn what is it Lets use a Template engine A template engine is
Mar 29, 2024 4 mins

TOC
Yo yo miss me right? Guess what Im back🥳🥳So lets talk about SSTI or Server-side template injection
As usually we need to works with things before jumping into SSTI. So lets try a template engine and learn what is it
Lets use a Template engine
A template engine is a software component designed to generate dynamic content based on a combination of pre-defined templates and data sources.

Bruh Let’s simplify this😂😂Basically, a template engine is a software component that generates dynamic content from our templates and fills the components of our template based on user data
ok so lets see a example
So im using jinja template engine for this
from flask import Flask,render_template_string
app = Flask(__name__)
@app.route('/hello/')
@app.route('/hello/<name>')
def hello(name=None):
return render_template_string("<h1>Hi!! "+name+"</h1>")this app directly renders user data without escape or anything so we can get xss out of this but we can fix this(and i didn’t)


Ok now we know little about template engine(I mean we don’t know lot of things about template engine)
so let’s see where ssti comes from
What is SSTI
Server-Side Template Injection (SSTI) is a type of security vulnerability that occurs when an attacker can inject and execute malicious code on the server-side template engine. This can lead to unauthorized access, data theft, and other malicious activities.

I know for first time who learn about ssti. this is harder to understand. so lets simplify this
in template engines we can run template syntaxes on it.
like this
from flask import Flask,render_template_string
app = Flask(__name__)
@app.route('/hello/')
@app.route('/hello/<name>')
def hello(name=None):
return render_template_string("{{3*3}}")the output will be like this

ok i think you are getting it.so do you remember i told you that there is a xss(also ssti) cause this app renders user data without any security method
from flask import Flask,render_template_string
app = Flask(__name__)
@app.route('/hello/')
@app.route('/hello/<name>')
def hello(name=None):
return render_template_string("<h1>Hi!! "+name+"</h1>")ok now lets see what will happen if we put template syntax into this

did you see that it rendered our syntax and gave us the result of 3*3 wich is 9🥳🥳
yeeah we injected a template syntax to the app and it rendered by the template engine
so ssti is a vuln where attacker can inject native template syntax payload to server side template and then it will execute on server side.now lets get RCE with SSTI
Remote Code execution
I know what are you thinking. youre thinking “we can just import the os module and get rce”.hmmm thats not gonna work.

so it wont work cause jinja isn’t allow to import modules in template native syntaxes. but don’t worry there is a way.
so you know everything object in python

thats right python is OOP lang and on python everything is a object

so lets try get access to the os module by accessing the objects

and lets keep going by accessing classes

ok now lets get all sub classes from base class

Okay, now what we need to do is to select a subclass that has sys modules.
so warnings.catch_warnings module uses sys module so Im gonna use it
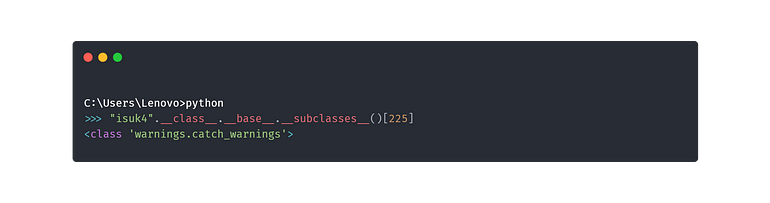
so lets access the sys module

so lets access os module

ok now lets run a command with this
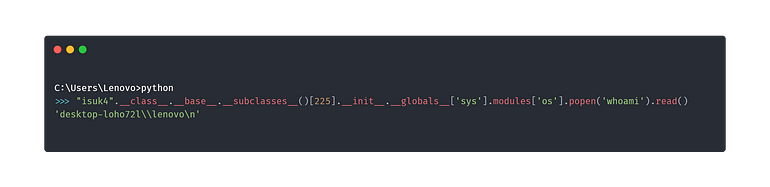
so lets do this in our web app and get our payload

and i got my payload
{{"isuk4".__class__.__base__.__subclasses__()[162].__init__.__globals__['sys'].modules['os'].popen('whoami').read()}}
so lets run this

so this is it SSTI.remember I only used jinja for this post there are other template engines
echo "so GGS!Ima off"so GGS!Ima off



