Payload will after you
Yo homies I’m back with another post.so lets start Before we dive into second order sql injection we need to talk about what is sql injecion What is Sql injection So Sql injection is attack that inject a malicious sql query to Application that can be execute SELECT
Mar 10, 2024 3 mins

TOC
Yo homies I’m back with another post.so lets start
Before we dive into second order sql injection we need to talk about what is sql injecion
What is Sql injection
So Sql injection is attack that inject a malicious sql query to Application that can be execute
SELECT * FROM `users` WHERE `name`='Isuk4' AND `pass`='Isuk4';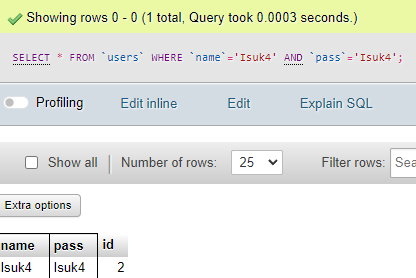
but what if attacker insert a sql query to this
SELECT * FROM `users` WHERE `name`=' ' OR '1' AND `pass`=' ' OR '1';
So I think you already know this.heeee
so lets deep dive into Second order sql injection
What is Second order attack
so in first order attack(i mean any first order attack) the payload will execute immediately but its different in second order attacks.in second order attacks payload will stored and execute after.🤢🤢

hmm let me tell this straight.so in second order attacks payload execute after like if we inject a payload and it will execute after in the application in other pages or other functions
I think you got that 😎
So I download a example page for second order sql injection
here is the link — https://github.com/riyazwalikar/sql-injection-training-app
ok I setup that and i went to the phpmyadmin and saw there is a user called admin so my mission is to get the admin password and get the admin user(although I can do it with phpmyadmin)
ok i went to second order example page

ok I now im trying to find is there a second order sql injection in this web(lol this a example application)
i tested it with add single quotes to inputs
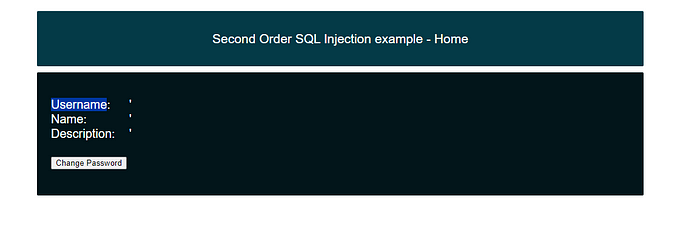
ok this page hasn’t a vuln.but when I went to “Change password” page i got this


hmm so found the vuln.so I need to achieve my goal
so I inject a payload for it
' or 1 in (select password from users where username='admin') – //
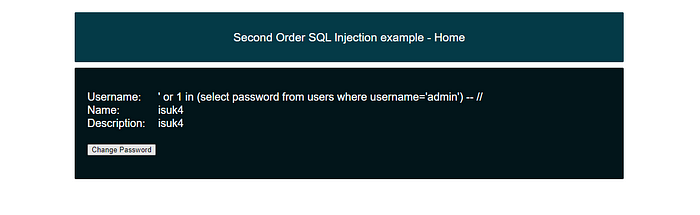

yeeah now all i need is decrypt this with MD5

yeeeah baby
so this is it.but remember this is a easy example real world applications can be different and hard to find vulns :-
so Ima off
echo "GGS! Ima off"


